SIEM setup
15-September-2025 + 14-October-2025 • Attacks & SIEM
Objective
set up splunk to log when things happen :)
Steps
Step 1
The lab setup needs its 'victim' machine to be monitored to forward its logs to Splunk. We're gonna use the Splunk Universal Forwarder for this - Splunk won't let me login from the VM's web browsers, so I downloaded it outside, downloaded OpenSSH again. (I allow it through the firewall, but it should be ok because in order to SSH in it'll ask for my login details.)

Step 2
here's our PuTTY command again (replace single ' with double quotes)
pscp 'C:\Users\jessr\Downloads\shared\splunkforwarder-10.0.0-windows-x64.msi' rui@192.168.0.48:C:\Users\rui\Downloads
Step 3
Now we setup to forward to our ubuntu server's static IP address (indexer? that's me!!! the ubuntu VM!)

Step 4
There are some config files to check here:
C:\Program Files\SplunkUniversalForwarder\etc\system\local\
Step 5
output.conf determines where to send logs.
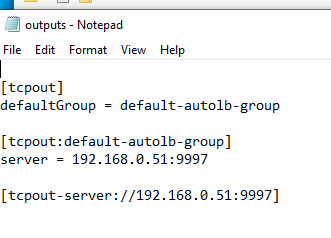
Step 6
We also are gonna make inputs.conf (to tell splunk which types of logs to send)

Step 7
Open cmd and restart the universal forwarder...
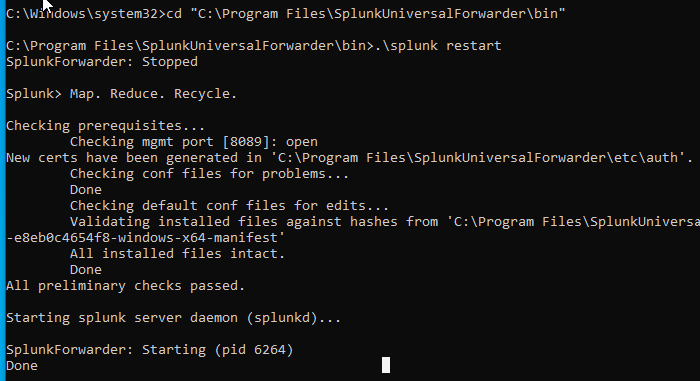
Step 8
Start the ubuntu server (VM) and login to splunk. Then we go to Settings > Forwarding/Receiving > Receive data > listen to port 9997, and save
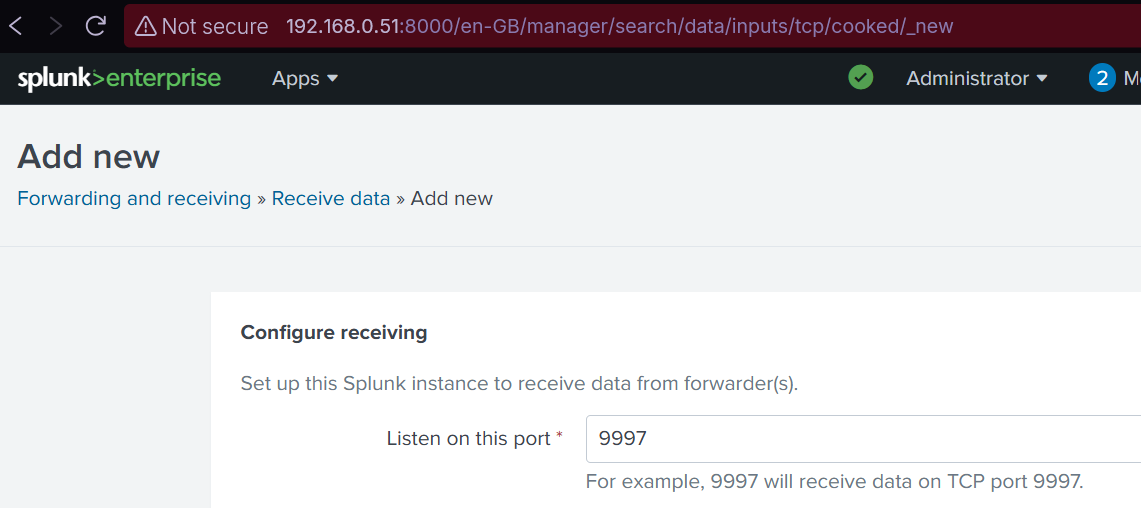
Step 9
on the endpoint (win10), we're gonna run this command to make sure the forwarder connected.
& 'C:\Program Files\SplunkUniversalForwarder\bin\splunk.exe' list forward-server
Step 10
It lists active forwards to my server VM static IP (allegedly), but I had some login issues. I stopped the server, deleted all users (deleting passwd.cong), reset my password using user-seed.conf, restarted the server... and finally, it listed active servers.
Step 11
we're gonna search splunk and... perfect!
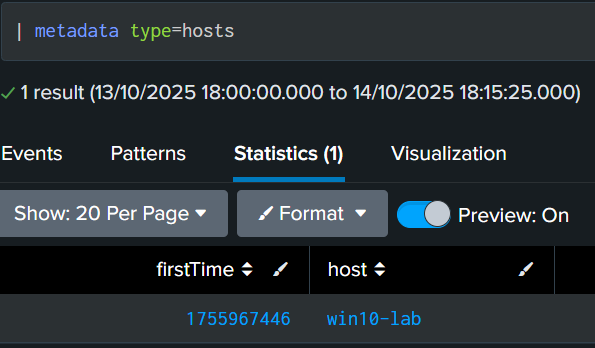
Step 12
We're gonna generate some events to test it out. First up: failed network login attempts (e.g. connecting to share files, or remote desktop) - open powershell on the victim computer and type this, which runs the command 5 times (log into my own IP address - 127.0.0.1 is a loopback - using IPC$ (interprocess communication) - using these credentials
for ($i=0; $i -lt 5; $i++) { cmd /c ''net use \\127.0.0.1\ipc$ /user:wronguser notpassword''' }
Step 13

Step 14
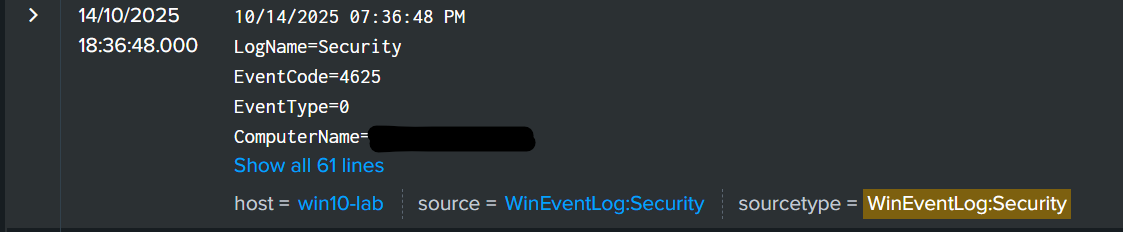
a failed login of this type comes up as event code 4625, so we can search that:
index=* sourcetype=''WinEventLog:Security'' EventCode=4625
Step 15
yes! that's me!
Step 16
all that troubleshooting took a little bit out of me, so I'm gonna go over some more events over the coming posts ;)
Notes / Lessons Learned
- Keep your passwords secure. 8+ characters, Aa + 123 + *