BTLO: Cerulean
21-August-2025 - present • capture the flag!
Objective
Dig through logs and form an attack timeline!
Steps
Step 1
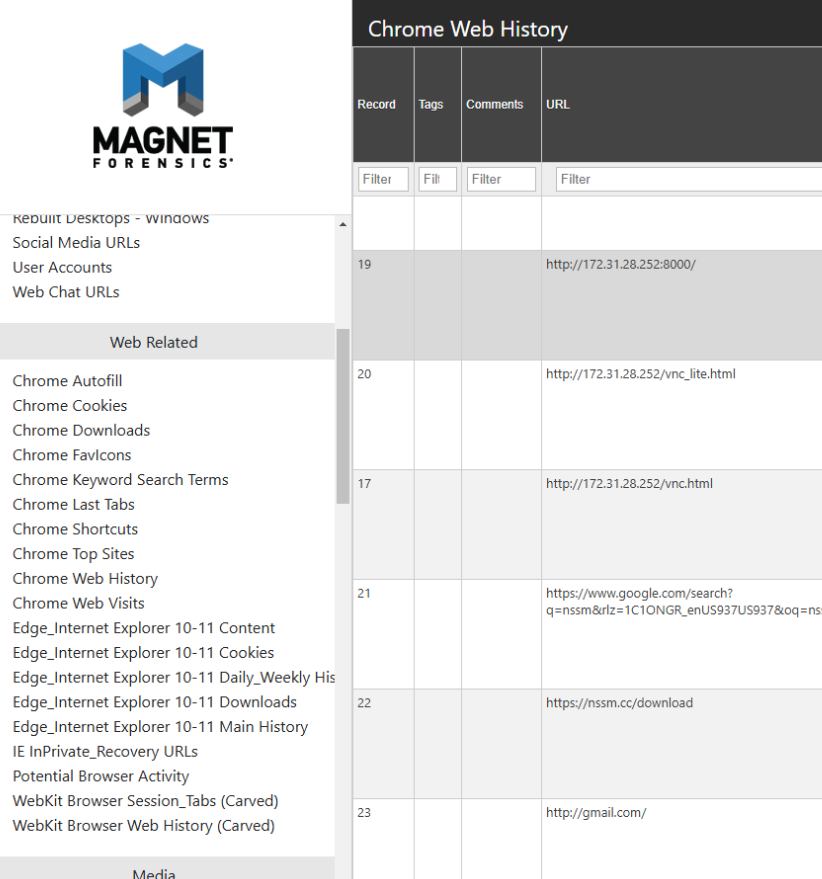
The situation: phishing scam with fake IT support. We can work this out from opening Magnet and looking at the web history - VNC (for remote connection), public IP addresses...
Step 2
Tried to build a timeline of events, but couldn't see earlier than the 'what's my IP address' search. Found a singular email but couldn't find any more leads. Checked local logs, appdata - notepads showed up garbled text. Eventually got frustrated and took a break.
Step 3
I found some writeups and took a note of the tools they used. (see sources.)
Step 4
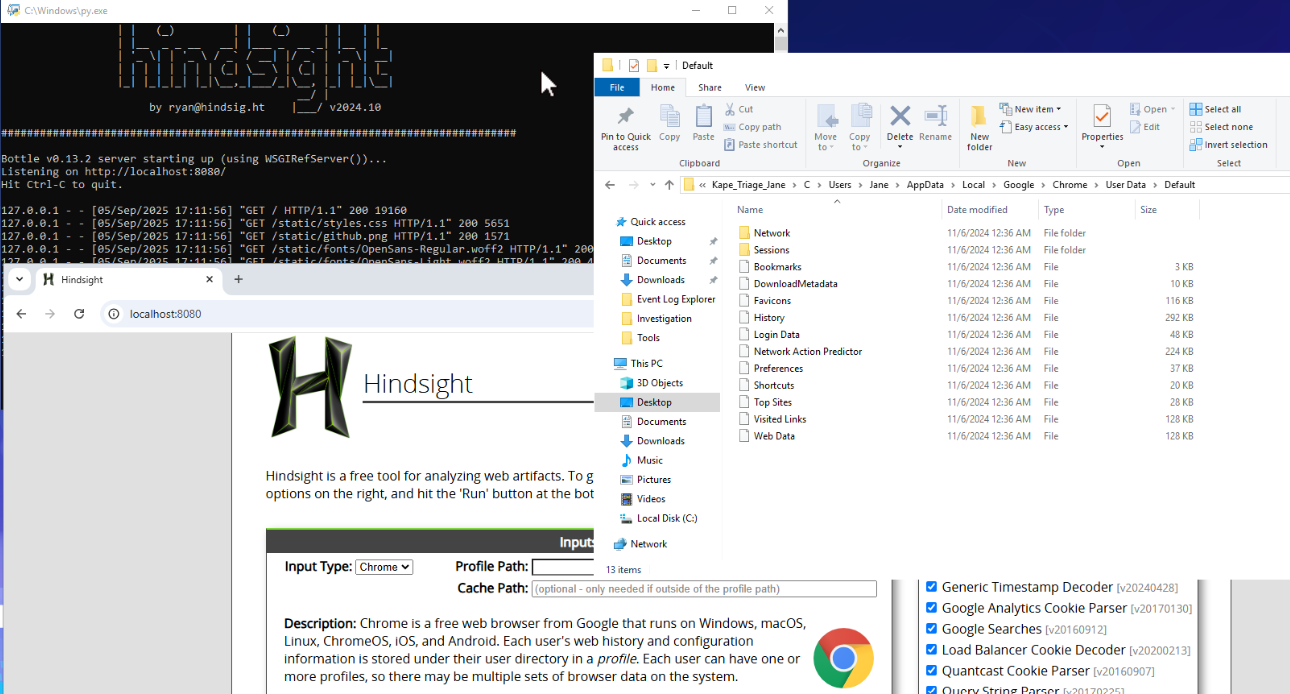
Started up hindsight gui (localhost:8080) and found Jane's chrome data directory.
Step 5
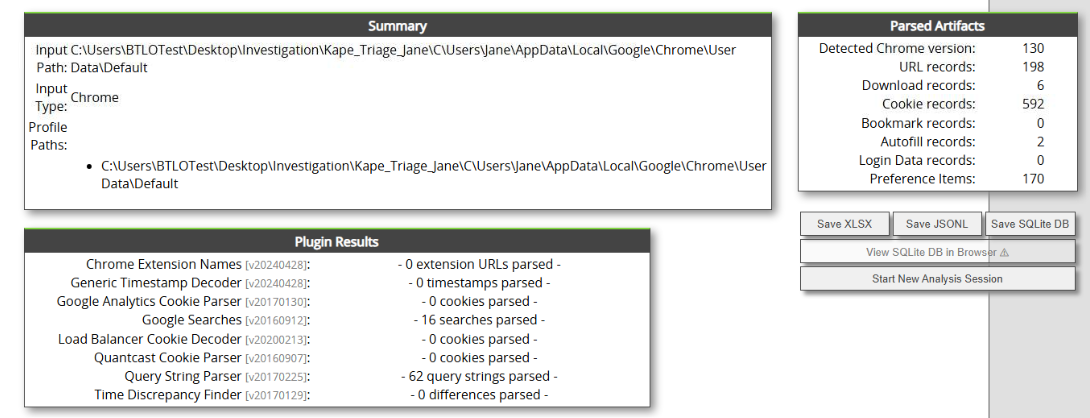
Awesome, we got a lot! Let's save it as xlsx so we can open it in timeline explorer.
Step 6
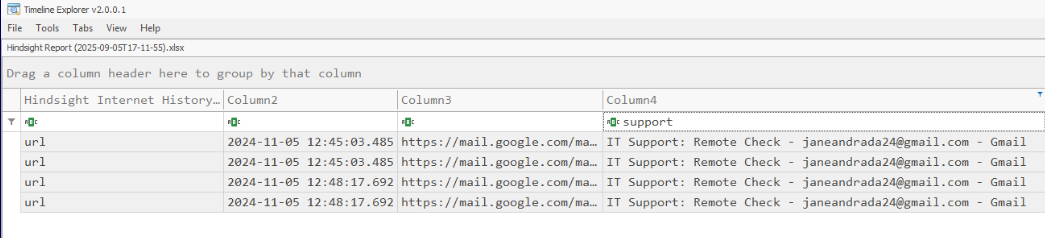
Q1. Open and search... magic!
Step 7
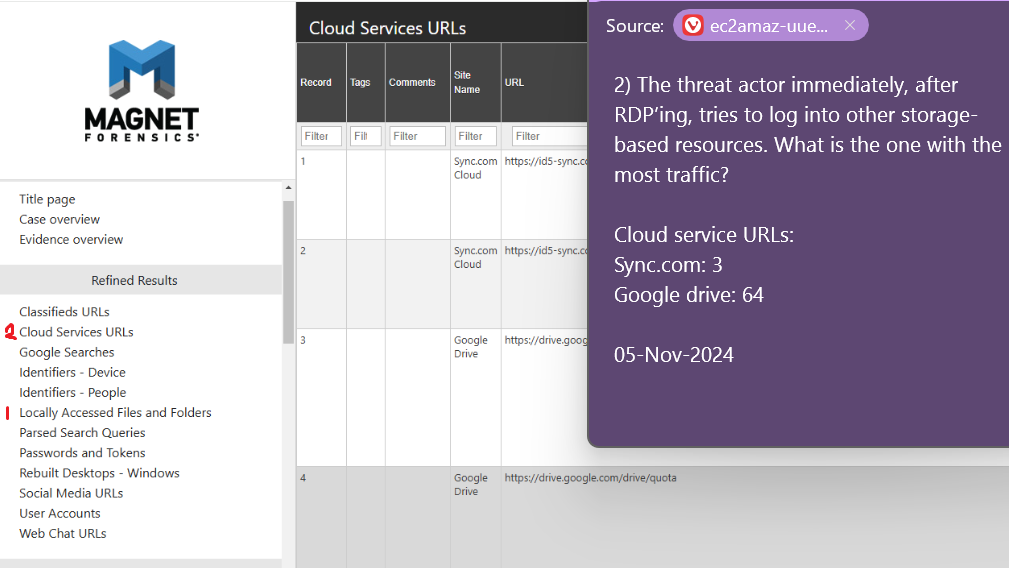
Q2. Opened magnet axiom. Checked locally accessed files first, but none matched the date of RDP. So I checked cloud service URLs... needless to say Google Drive was a little popular
Step 8
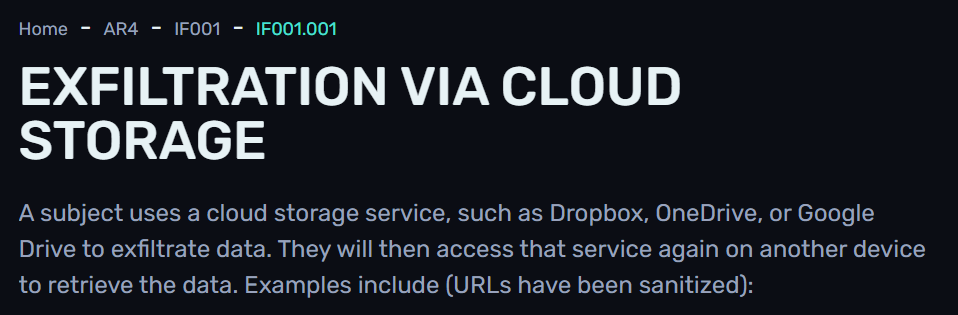
Q3. Today I learned about inside threat matrix. There's a code for every threat.
Step 9
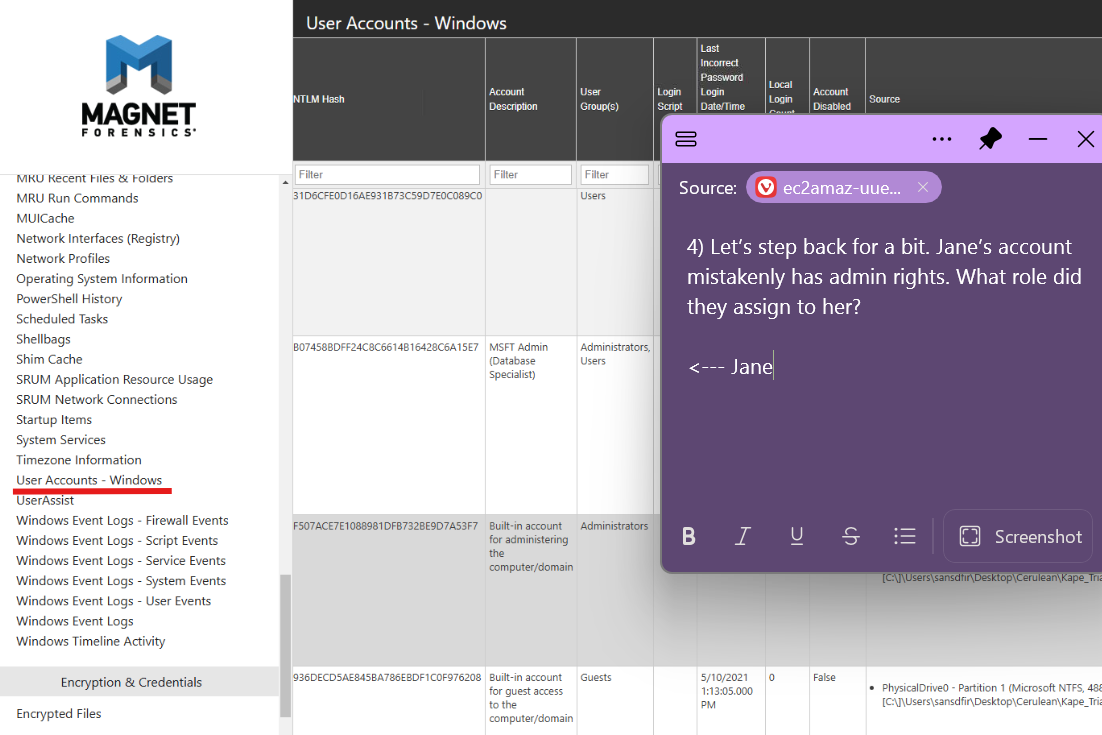
Q4. Luckily magnet lets us peek at all the computer's accounts too!
Step 10
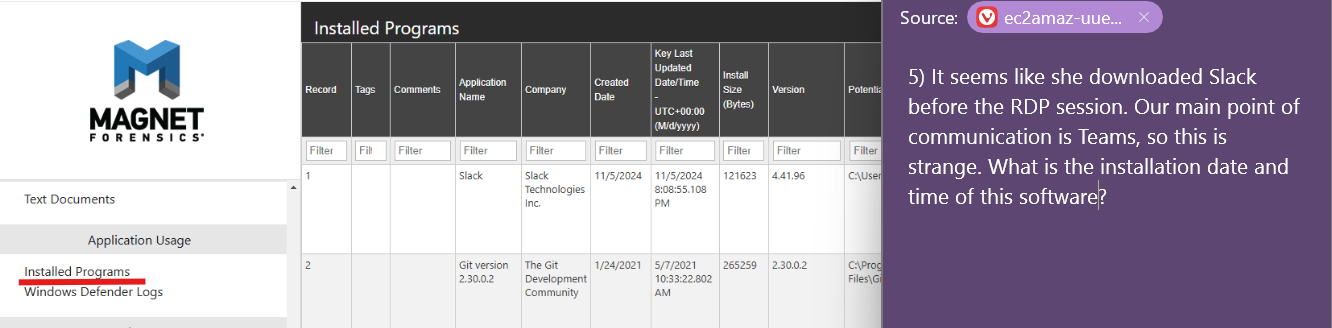
Q5. It even tells us what programs were installed when! -- same date as the remote access session? suspicious.
Step 11
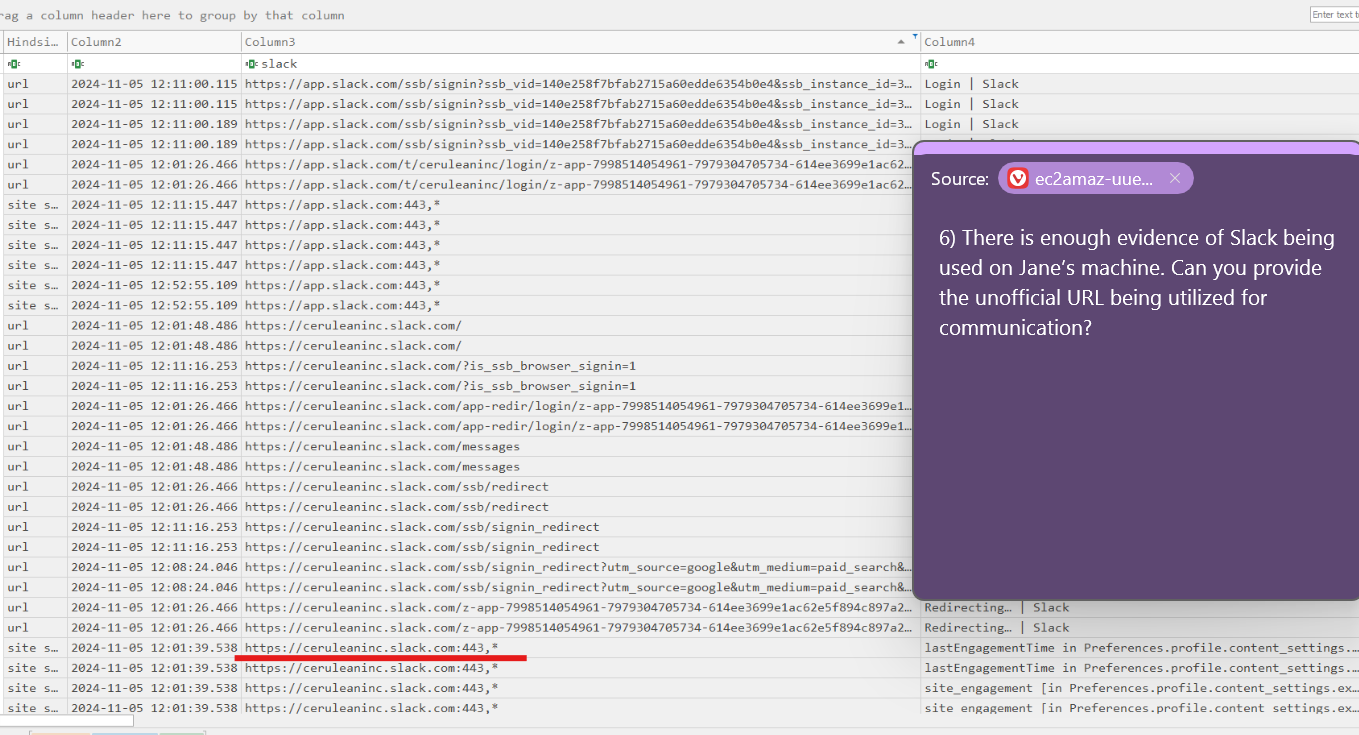
Q6. Back to our best friend, timeline explorer. URL search for slack... everything looks okay. Oh, cerulean is in the URL- is that a port number at the end?? sus bro!! a port number means communication with slack's servers (when this machine shouldn't really be using slack at all).
Step 12
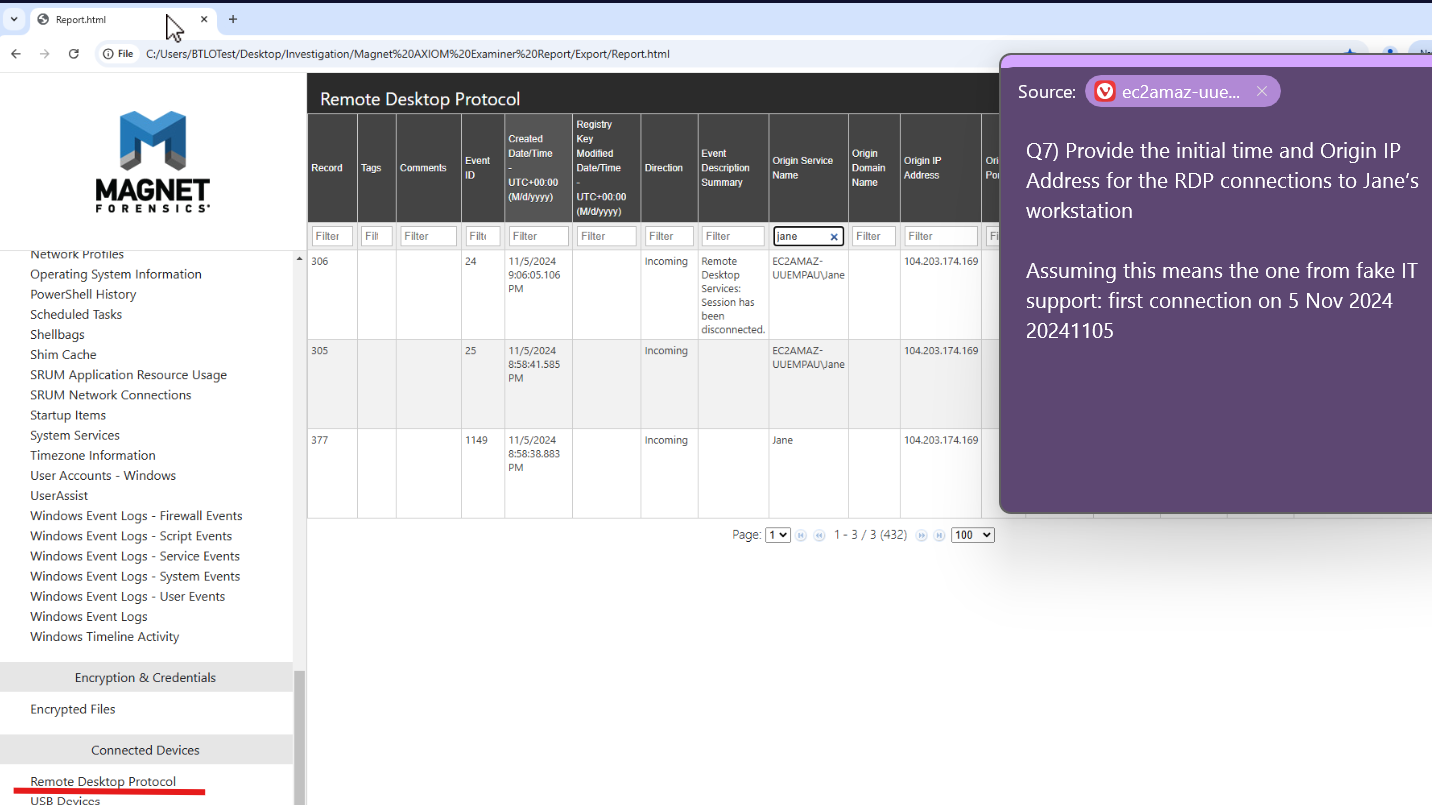
Q7. taking a look at magnet and RDP. I found it tricky to search by date, but we can see by origin (Jane) just fine.
Notes / Lessons Learned
- asking for help is fine.